Hi everyone,
I was hired a few months ago to configure Linux CentOS 7 distrib for a customer to authenticate his Administrator with his Windows domain credentials.
Not really difficult, but depending of your Linux Distrib it can be difficult to find all the information needed.
Linux Client
On the Linux side, you must have a Radius client to communicate with your Radius Server. So first you must install and configure this client.
To check what package you must install, use the following :
yum list *radius*
then install your packet, in my case :
yum install pam_radius.x86_64
Ok, now provide access to the radius client file :
chmod 0600 /etc/pam_radius.conf
In the same file, add the Radius Server’s IP and your shared secret (see the other chapter) :
vi /etc/pam_radius.conf #server:[port] shared_secret timeout (s) 192.179.30.10 mysharesecretkey 5
You must add the username using the following :
useradd myuser
or
useradd -ou 0 -g 0 myuser
The username must be the same than the one in your Active Directory without “domain\”
Then you must add the possibility to your user to use radius authentication through SSH by configuring SSH adding the following :
vi /etc/pam.d/sshd auth sufficient /usr/lib64/security/pam_radius_auth.so
Restart using service sshd restart
Windows Network Policy Server
On the Network Policy Server, you must start by configuring a Radius Client (your Linux Server) and generate a shared secret :
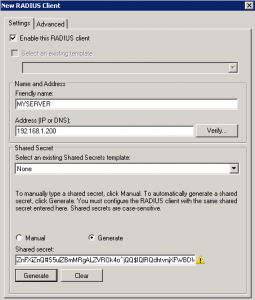
Then in network Policies node you must create a new Policy (Grant Access) :
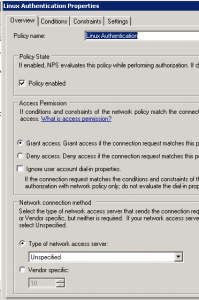
Add your Windows Admin Groups in “Windows Groups” panel :
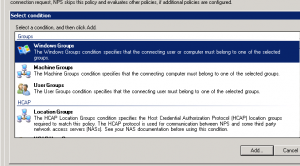
Then configure the Authentication Method in our case, must be “Unencrypted Authentication” :
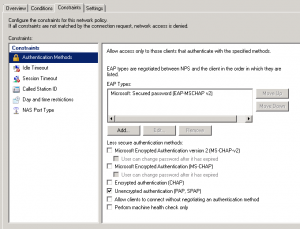
Now, your NPS is configured. Back to your Putty, you can try to connect to your Linux Server using your Active Directory username and password.
If you have some problem to authenticate, you can use NPS logs to troubleshoot. To configure the log path, use in NPS console and then localize in Accounting the log path : NPS EventID
Go further
Your authentication works, but you have some stuff to do before putting this into production. See some point you must keep in mind to enhance the security :
- Once your authentication is OK, it is a good practice to disable the “root” authentication through SSH (from sshd file configuration).
PermitRootLogin no
- The account created has no right even if you do a su, configure your account to have what you need. For example the same right than a root (not recommended) or right to use su and run with the root account.
usermod -ou 0 -g 0 yourusername
or
usermod -a -G sudo yourusername
- On your NPS server you can create a Shared Secrets Template to have the same Secret for your Linux Server and copy the pam file to configure all of your Linux server. Very usefull to renew Shared Secret more often.
- Configure auditing to have a log of privileged access on your server
#file configuration /etc/audit/auditd.conf #You can increause the number of audit log file num_logs = 30 max_log_file = 30 max_log_file_action = ROTATE #Log file location /var/log/audit/audit.log @restart the service service auditd restart @looking in search log file for LOGIN ausearch -m LOGIN --start today -i #A specific eventID ausearch -a 27020 #Extract a report aureport --failed
I hope this article helps you to configure more securely your Linux SSH access with your Active Directory credential.
